# Otomi
**Repository Path**: micoder/Otomi
## Basic Information
- **Project Name**: Otomi
- **Description**: Otomi 是一个基于 Kubernetes 的开源平台,它提供了类似于 Linux 桌面环境的用户界面,使用者可以像部署 Linux 中的软件包一样部署 Kubernetes 中
- **Primary Language**: JavaScript
- **License**: Apache-2.0
- **Default Branch**: main
- **Homepage**: https://www.oschina.net/p/otomi
- **GVP Project**: No
## Statistics
- **Stars**: 0
- **Forks**: 2
- **Created**: 2021-11-25
- **Last Updated**: 2024-01-18
## Categories & Tags
**Categories**: Uncategorized
**Tags**: None
## README

Self-hosted DevOps Platform for Kubernetes









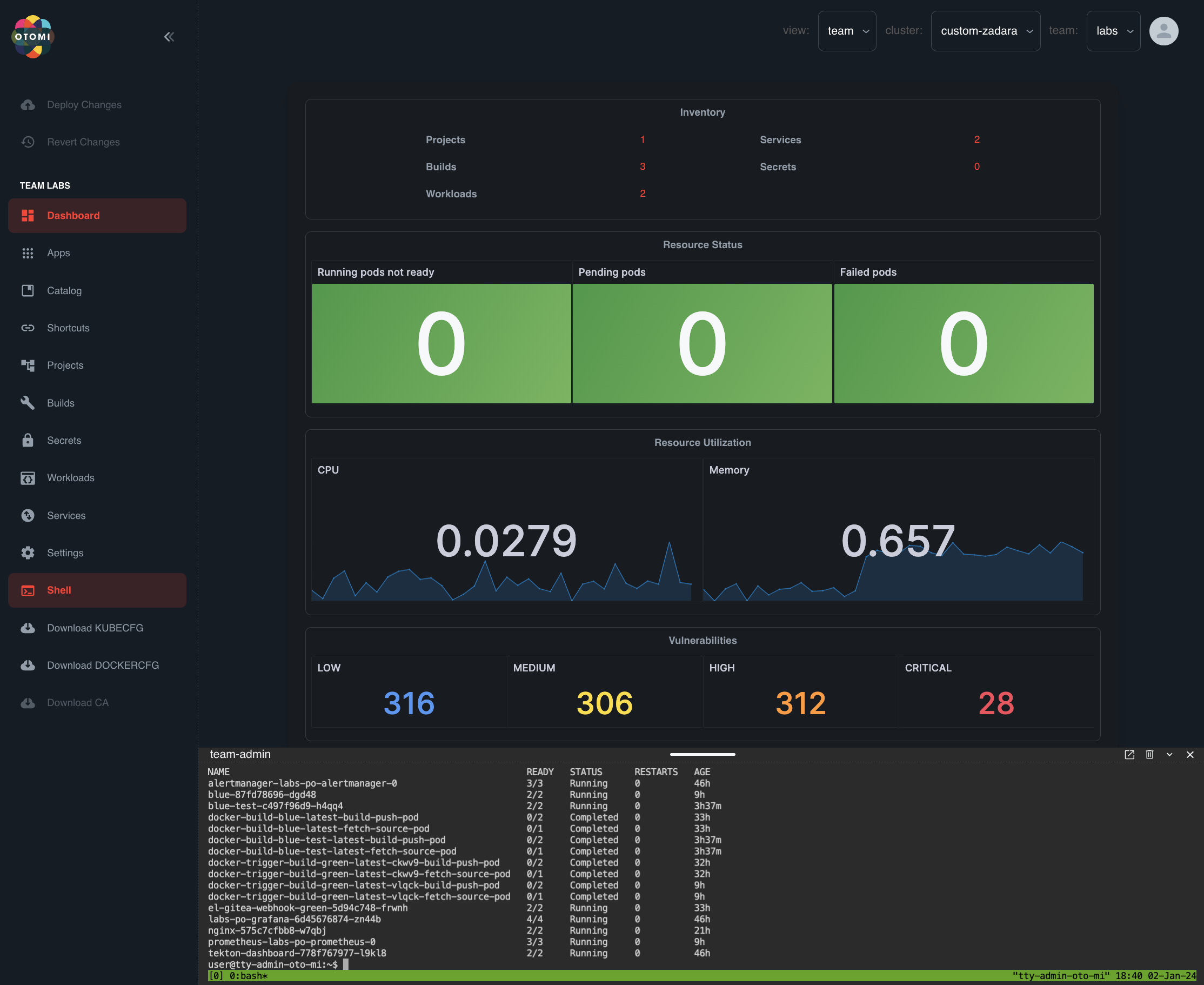
Otomi turns any Kubernetes cluster into a DevOps Platform to provide paved roads from code to production
## How Otomi helps
**DevOps Teams** - With self-service, automation and visibility to let them take full-service ownership
- Create private Git repositories
- Build OCI compliant images from application code and store them in a private registry
- Deploy containerized workloads using a catalog with pre-filled golden path templates
- Automatically update container images of workloads
- Publicly expose applications
- Get instant access to logs, metrics and traces, vulnerabilities, threads and policy violations
- Configure network policies, response headers and CNAMEs
- Manage secrets
**Platform teams** - To setup a Kubernetes-based platform for DevOps teams and provide them a paved road to production
- Create a platform profile and deploy to any Kubernetes cluster
- Onboard DevOps teams in a comprehensive multi-tenant setup and allow them to take full ownership over their applications
- Get all the required capabilities in an integrated and automated way
- Ensure governance with security policies
- Implement zero-trust networking
- Change the desired state of the platform based on Configuration-as-Code
- Support multi- and hybrid cloud scenarios
- Prevent cloud provider lock-in
- Implement full observability
- Create Golden path templates and offer them to DevOps teams through a catalog
## Getting started
### Helm
To install Otomi, make sure to have a K8s cluster running with at least:
- Version `1.25`, `1.26` or `1.27`
- A node pool with at least **8 vCPU** and **16GB+ RAM** (more resources might be required based on the activated capabilities)
- Calico CNI installed (or any other CNI that supports K8s network policies)
- A default storage class configured
- When using the `custom` provider, make sure the K8s LoadBalancer Service created by `Otomi` can obtain an external IP (using a cloud load balancer or MetalLB)
> **_NOTE:_** Install Otomi with DNS to unlock it's full potential. Check [otomi.io](https://otomi.io) for more info.
Add the Helm repository:
```bash
helm repo add otomi https://otomi.io/otomi-core
helm repo update
```
and then install the Helm chart:
```bash
helm install otomi otomi/otomi \
--set cluster.name=$CLUSTERNAME \
--set cluster.provider=$PROVIDER # use 'azure', 'aws', 'google', 'digitalocean', 'ovh', 'vultr', 'scaleway', 'civo', or 'custom' for any other cloud or onprem K8s
```
When the installer job is completed, follow the [activation steps](https://otomi.io/docs/get-started/activation).
## Platform architecture
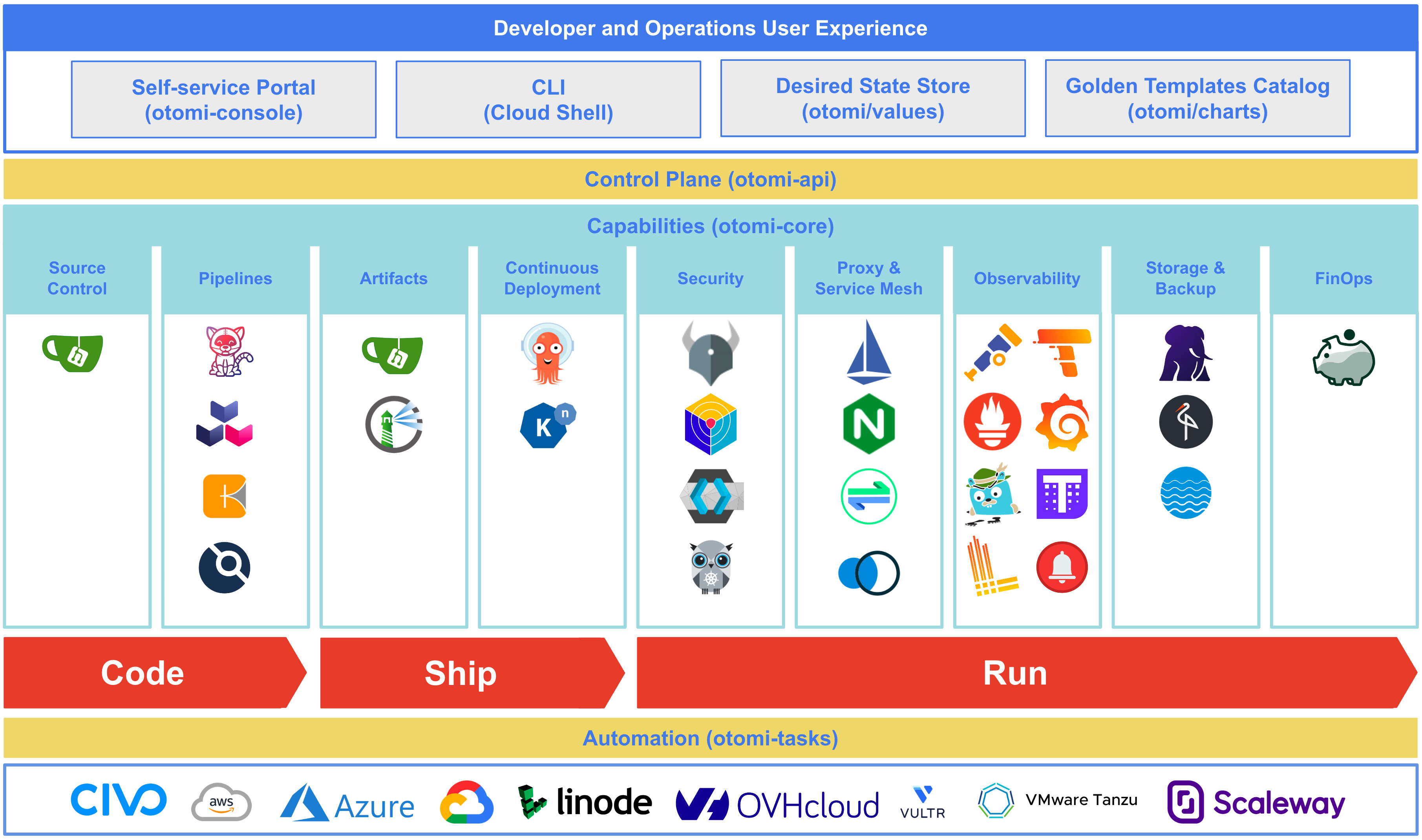
### Self-service portal and Cloud Shell
The self-service portal (Otomi Console) offers seamless user experience for DevOps teams and platform administrators. Platform administrators can use Otomi Console to enable and configure platform capabilities and onboard development teams. DevOps teams can use Otomi Console to build images, deploy applications, expose services, configure CNAMEs, configure network policies and manage secrets. Otomi Console also provided direct and context aware access to platform capabilities like code repositories, registries, logs, metrics, traces, dashboards, etc. Next to the web based self-service, both teams and admins can start a Cloud Shell and run CLI commands.
### Desired state store
When Otomi is installed, the desired state of the platform is stored in the `otomi/values` Git repository. Changes made through the Console will be reflected in the repository.
### Golden path templates Catalog
The `otomi/charts` Git repo includes a set of build-in Helm charts that can be used to create workloads in the Console. You can also add your own charts and offer them to the teams on the platform.
### Control plane
All changes made through the Console are validated by the control plane (`otomi-api`) and then committed in Git. This will automatically trigger the platform to synchronize the desired state to the actual state of the platform based on GitOps.
### Automation
The automation (operator) is used to synchronize desired state with the state of applications like Keycloak, Harbor and Gitea.
### Capabilities
Otomi offers a set of Kubernetes applications for all the required platform capabilities. Core applications are always installed, optional applications can be activated. When an application is activated, the application will be installed based on a configuration profile that contains defaults, best-practices and platform integrations. Default configuration can be adjusted using the Console.
**Core Applications (that are always installed):**
- [Istio](https://github.com/istio/istio): The service mesh framework with end-to-end transit encryption
- [Argo CD](https://github.com/argoproj/argo-cd): Declarative Continuous Deployment
- [Keycloak](https://github.com/keycloak/keycloak): Identity and access management for modern applications and services
- [Cert Manager](https://github.com/cert-manager/cert-manager) - Bring your own wildcard certificate or request one from Let's Encrypt
- [Nginx Ingress Controller](https://github.com/kubernetes/ingress-nginx): Ingress controller for Kubernetes
- [External DNS](https://github.com/kubernetes-sigs/external-dns): Synchronize exposed ingresses with DNS providers
- [Tekton Pipeline](https://github.com/tektoncd/pipeline): K8s-style resources for declaring CI/CD pipelines
- [Tekton Triggers](https://github.com/tektoncd/triggers): Trigger pipelines from event payloads
- [Tekton dashboard](https://github.com/tektoncd/dashboard): Web-based UI for Tekton Pipelines and Tekton Triggers
- [Gitea](https://github.com/go-gitea/gitea): Self-hosted Git service
- [Cloudnative-pg](https://github.com/cloudnative-pg/cloudnative-pg): Open source operator designed to manage PostgreSQL workloads
- [Paketo build packs](https://github.com/paketo-buildpacks): Cloud Native Buildpack implementations for popular programming
- [Kaniko](https://github.com/GoogleContainerTools/kaniko): Build container images from a Dockerfile
**Optional Applications (that you can activate to compose your ideal platform):**
- [Velero](https://github.com/vmware-tanzu/velero): Back up and restore your Kubernetes cluster resources and persistent volumes
- [Knative](https://github.com/knative/serving): Deploy and manage serverless workloads
- [Drone](https://github.com/harness/drone): Continuous integration platform built on Docker
- [Prometheus](https://github.com/prometheus/prometheus): Collecting container application metrics
- [Grafana](https://github.com/grafana/grafana): Visualize metrics, logs, and traces from multiple sources
- [Grafana Loki](https://github.com/grafana/loki): Collecting container application logs
- [Harbor](https://github.com/goharbor/harbor): Container image registry with role-based access control, image scanning, and image signing
- [HashiCorp Vault](https://github.com/hashicorp/vault): Manage Secrets and Protect Sensitive Data
- [OPA/Gatekeeper](https://github.com/open-policy-agent/gatekeeper): Policy-based control for cloud-native environments
- [Jaeger](https://github.com/jaegertracing/jaeger): End-to-end distributed tracing and monitor for complex distributed systems
- [Kiali](https://github.com/kiali/kiali): Observe Istio service mesh relations and connections
- [Minio](https://github.com/minio/minio): High performance Object Storage compatible with Amazon S3 cloud storage service
- [Trivy](https://github.com/aquasecurity/trivy-operator): Kubernetes-native security toolkit
- [Thanos](https://github.com/thanos-io/thanos): HA Prometheus setup with long term storage capabilities
- [Falco](https://github.com/falcosecurity/falco): Cloud Native Runtime Security
- [Opencost](https://github.com/opencost/opencost): Cost monitoring for Kubernetes
language ecosystems
- [Grafana Tempo](https://github.com/grafana/tempo): High-scale distributed tracing backend
- [OpenTelemetry](https://github.com/open-telemetry/opentelemetry-operator): Instrument, generate, collect, and export telemetry data to help you analyze your software’s performance and behavior
### Supported providers
Otomi can be installed on any Kubernetes cluster. At this time, the following providers are supported:
- `aws` for [AWS Elastic Kubernetes Service](https://aws.amazon.com/eks/)
- `azure` for [Azure Kubernetes Service](https://azure.microsoft.com/en-us/products/kubernetes-service)
- `google` for [Google Kubernetes Engine](https://cloud.google.com/kubernetes-engine?hl=en)
- `linode` for [Linode Kubernetes Engine](https://www.linode.com/products/kubernetes/)
- `ovh` for [OVH Cloud](https://www.ovhcloud.com/en/public-cloud/kubernetes/)
- `vultr` for [Vultr Kubernetes Engine](https://www.vultr.com/kubernetes/)
- `scaleway` for [Scaleway Kapsule](https://www.scaleway.com/en/kubernetes-kapsule/)
- `civo` for [Civo Cloud K3S](https://www.civo.com/)
- `custom` for any other cloud/infrastructure
## Otomi Projects
Otomi open source consists out of the following projects:
- Otomi Core (this project): The heart of Otomi
- [Otomi Tasks](https://github.com/redkubes/otomi-tasks): Autonomous jobs orchestrated by Otomi Core
- [Otomi Clients](https://github.com/redkubes/otomi-clients): Factory to build and publish openapi clients used in by otomi-tasks
## Documentation
Check out the [dev docs index](./docs/README.md) for developer documentation or go to [otomi.io](https://otomi.io) for more detailed documentation.
## Contribution
If you wish to contribute please read our [Contributor Code of Conduct](https://otomi.io/community/code-of-conduct) and [Contribution Guidelines](https://otomi.io/community/get-involved).
If you want to say **thank you** or/and support the active development of Otomi:
- [Star](https://github.com/redkubes/otomi-core) the Otomi project on Github
- Feel free to write articles about the project on [dev.to](https://dev.to/), [medium](https://medium.com/) or on your personal blog and share your experiences
This project exists thanks to all the people who have contributed
 ## License
Otomi is licensed under the [Apache 2.0 License](https://github.com/redkubes/otomi-core/blob/main/LICENSE).
## License
Otomi is licensed under the [Apache 2.0 License](https://github.com/redkubes/otomi-core/blob/main/LICENSE).


